
Data and identity theft is a serious and growing threat.
According to a survey by independent market research company StrategyOne, commissioned by Symantec, 65% of all people globally have been victims of computer crime, which caused considerable damage. McAffee estimates the damage worldwide to $ 1 trillion annually.
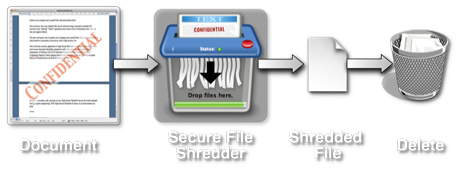
Basic "delete" operations only remove bits of information from files, so they just appear deleted. It is easy to retrieve those files with common file recovery tools.
And even simple overwritten data can be recovered using sophisticated tools, such as magnetic force microscopes. One standard way to recover data that has been overwritten is to capture and process the analog signal obtained from the hard drive's read/write head. This analog signal will be close to an ideal digital signal, but the differences will reveal important information.
 |
 |
 |
| Basis "delete" operation ( unsecure ) |
Simple overwriten ( unsecure ) |
Shredding ( secure ) |
Secure Deletion:
The only way to protect your company and yourself from data or identity theft is to shred sensitive documents at the source with a high security tool that is capable of rewriting the files with random series of binary data multiple times.
High Secure Shredder
One of the most secure file shredding application is High Secure Shredder. It supports the most secure document shredding standards world wide, including the United States Department of Defense 5220.22-M National Industrial Security Standard, the USAF Cryptologic Support Center purging Standard and the Gutmann method.
Reliable, convenient, safe, and easy-to-use, High Secure Shredder has set the world standard for high quality engineering. With High Secure Shredder all traces of your documents are gone.

Protect your company and yourself
from data and identity theft.
Did you know, how easy deleted files can be retrieved using commonly available file recovery tools?
Ordinary "delete" operations only remove bits of information from files, so they just appear deleted. Even simple overwritten data can be recovered using sophisticated tools. ( Why shred files? )
The only and surest way to protect your company and yourself from data or identity theft is to shred sensitive documents at the source with a high security tool.
One of the best security application is High Secure Shredder. It supports the most secure document shredding standards world wide, including
- The United States Department of Defense 5220.22-M National Industrial Security Standard,
- The USAF Cryptologic Support Center purging Standard and
- The Gutmann method.
And a detailed report keep you informed about all shred activities at any time.
Reliable, convenient, safe, and easy-to-use, High Secure Shredder has set the world standard for high quality engineering. With High Secure Shredder all traces of your documents are gone.
High Secure Shredder key features:
| ◊ | Detailed status reporting about all shred activities. |
| ◊ | Meets the high secure document shredding standards, including AFSSI-5020, DoD 5220.22-M, Zero Out, Quick and Gutmann. |
| ◊ | Additional overwriting with ASCII data |
| ◊ | Visual and audio feedback. |
| ◊ | Drag & Drop support to easily shred mass of files. |
| ◊ | Detailed reporting about all shred activities. |
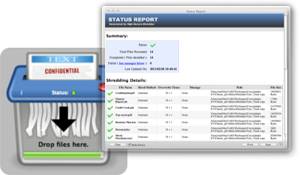
High Secure Shredder Status Report
| With the High Secure Shredder Status Report you are always informed about all shred activities. The report helps you to figure out what's going on while shredding files, it enables you to identify errors and suggest corrective actions. |
 |
High Secure Shredder system requirements
- Mac OS X Version 10.6.6 (Snow Leopard) or later.
- Intel Mac.

Gutmann method
35 pass overwrite data
Basic "delete" operations only remove bits of information from files, so they just appear deleted, and even overwritten data can be recovered using sophisticated tools, like magnetic force microscopes.
The only way to protect your company and yourself from data or identity theft is to shred sensitive documents and files with a high security tool that is capable of rewriting the files with random series of binary data multiple times.
The Gutmann method is an algorithm for securely erasing the contents of documents and files. It destroys the magnetic memory by writing a series of 35 patterns over the entire region to be erased. This method provides highly effective security against the recovery of data.

Overwrite patterns chart
|
Gutmann method
( 35 pass overwrite data ) |
|||||
| Pass
|
Data written | Encoding scheme targeted
|
|||
| Binary notation | Hexadecimal notation | ||||
| 1 | Random | Random | |||
| 2 | Random | Random | |||
| 3 | Random | Random | |||
| 4 | Random | Random | |||
| 5 | 01010101 01010101 01010101 | 55 55 55 | (1,7) RLL | MFM | |
| 6 | 10101010 10101010 10101010 | AA AA AA | (1,7) RLL | MFM | |
| 7 | 10010010 01001001 00100100 | 92 49 24 | (2,7) RLL | MFM | |
| 8 | 01001001 00100100 10010010 | 49 24 92 | (2,7) RLL | MFM | |
| 9 | 00100100 10010010 01001001 | 24 92 49 | (2,7) RLL | MFM | |
| 10 | 00000000 00000000 00000000 | 00 00 00 | (1,7) RLL | (2,7) RLL | |
| 11 | 00010001 00010001 00010001 | 11 11 11 | (1,7) RLL | ||
| 12 | 00100010 00100010 00100010 | 22 22 22 | (1,7) RLL | ||
| 13 | 00110011 00110011 00110011 | 33 33 33 | (1,7) RLL | (2,7) RLL | |
| 14 | 01000100 01000100 01000100 | 44 44 44 | (1,7) RLL | ||
| 15 | 01010101 01010101 01010101 | 55 55 55 | (1,7) RLL | MFM | |
| 16 | 01100110 01100110 01100110 | 66 66 66 | (1,7) RLL | (2,7) RLL | |
| 17 | 01110111 01110111 01110111 | 77 77 77 | (1,7) RLL | ||
| 18 | 10001000 10001000 10001000 | 88 88 88 | (1,7) RLL | ||
| 19 | 10011001 10011001 10011001 | 99 99 99 | (1,7) RLL | (2,7) RLL | |
| 20 | 10101010 10101010 10101010 | AA AA AA | (1,7) RLL | MFM | |
| 21 | 10111011 10111011 10111011 | BB BB BB | (1,7) RLL | ||
| 22 | 11001100 11001100 11001100 | CC CC CC | (1,7) RLL | (2,7) RLL | |
| 23 | 11011101 11011101 11011101 | DD DD DD | (1,7) RLL | ||
| 24 | 11101110 11101110 11101110 | EE EE EE | (1,7) RLL | ||
| 25 | 11111111 11111111 11111111 | FF FF FF | (1,7) RLL | (2,7) RLL | |
| 26 | 10010010 01001001 00100100 | 92 49 24 | (2,7) RLL | MFM | |
| 27 | 01001001 00100100 10010010 | 49 24 92 | (2,7) RLL | MFM | |
| 28 | 00100100 10010010 01001001 | 24 92 49 | (2,7) RLL | MFM | |
| 29 | 01101101 10110110 11011011 | 6D B6 DB | (2,7) RLL | ||
| 30 | 10110110 11011011 01101101 | B6 DB 6D | (2,7) RLL | ||
| 31 | 11011011 01101101 10110110 | DB 6D B6 | (2,7) RLL | ||
| 32 | Random | Random | |||
| 33 | Random | Random | |||
| 34 | Random | Random | |||
| 35 | Random | Random | |||
RLL : Run Length Limited
MFM : Modified Frequency Modulation
See also:
Peter Gutmann http://www.cs.auckland.ac.nz/~pgut001/pubs/secure_del.html

DoD 5220.22-M Standard
Seven pass overwrite data
Basic "delete" operations only remove bits of information from files, so they just appear deleted, and even overwritten data can be recovered using sophisticated tools, like magnetic force microscopes.
The only way to protect your company and yourself from data or identity theft is to shred sensitive documents and files with a high security tool that is capable of rewriting the files with random series of binary data multiple times.
The United States Department of Defense 5220.22-M National Industrial Security Standard writes series of seven patterns over the entire region to be erased. This provides a highly secure erasure of disk data.
Overwrite patterns chart
|
DoD 5220.22-M Standard
( 7 pass overwrite data ) |
||
| Pass |
Data written
|
|
| Binary notation | Hexadecimal notation | |
| 1 | 11110110 | 0xF6 |
| 2 | 00000000 | 0x00 |
| 3 | 11111111 | 0xFF |
| 4 | Random | Random |
| 5 | 00000000 | 0x00 |
| 6 | 11111111 | 0xFF |
| 7 | Random | Random |
{mospagebreak title=AFSSI-5020}

AFSSI-5020 Standard
Three pass overwrite data
Basic "delete" operations only remove bits of information from files, so they just appear deleted, and even overwritten data can be recovered using sophisticated tools, like magnetic force microscopes.
The only way to protect your company and yourself from data or identity theft is to shred sensitive documents and files with a high security tool that is capable of rewriting the files with random series of binary data multiple times.
AFSSI-5020 is the USAF Cryptologic Support Center purging standard from 1996. It writes series of three patterns over the entire region to be erased. This option provides very good data security by optimal performance.
Overwrite patterns chart
|
AFSSI-5020 Standard
( 3 pass overwrite data ) |
||
| Pass |
Data written
|
|
| Binary notation | Hexadecimal notation | |
| 1 | 00000000 | 0x00 |
| 2 | 11111111 | 0xFF |
| 3 | Random | Random |

AFSSI-5020 Standard
Three pass overwrite data
Basic "delete" operations only remove bits of information from files, so they just appear deleted, and even overwritten data can be recovered using sophisticated tools, like magnetic force microscopes.
The only way to protect your company and yourself from data or identity theft is to shred sensitive documents and files with a high security tool that is capable of rewriting the files with random series of binary data multiple times.
AFSSI-5020 is the USAF Cryptologic Support Center purging standard from 1996. It writes series of three patterns over the entire region to be erased. This option provides very good data security by optimal performance.

Overwrite patterns chart
|
AFSSI-5020 Standard
( 3 pass overwrite data ) |
||
| Pass |
Data written
|
|
| Binary notation | Hexadecimal notation | |
| 1 | 00000000 | 0x00 |
| 2 | 11111111 | 0xFF |
| 3 | Random | Random |
Want to try before you buy?
Whether you are looking for software for a specific project, or just want to flex your creative muscles and try something new, our collection of jalada software has something for everyone. And the best part? You can download a fully functional trial version for FREE!
You can now download your trial software by clicking the button for your operating system below.